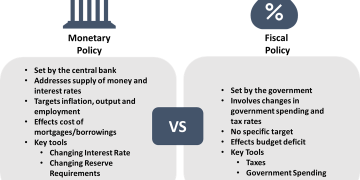
Executive Summary
Information warfare is no longer a future threat—it is a present and persistent challenge. This report examines the strategies that governments, corporations, and civil societies can employ to protect themselves from IW.
It highlights three pillars of defense: technological safeguards, policy frameworks, and societal resilience.
I. The Changing Nature of Conflict
- Hybrid Warfare: Modern conflicts blend physical attacks with digital and cognitive operations.
- Perception as a Battleground: Winning hearts and minds can now outweigh physical victories.
- Persistent Engagement: IW campaigns are continuous, not confined to wartime.
II. Threat Landscape
- State Actors: Use coordinated cyber tools and propaganda to destabilize rivals.
- Non-State Groups: Terrorist and extremist networks manipulate online platforms for recruitment and funding.
- Corporate Espionage: Private-sector data theft for competitive advantage.
- Algorithmic Exploits: Manipulation of recommendation engines to spread divisive content.
III. Strategic Response Framework
A multi-dimensional defense strategy is essential.
1. Technological Safeguards
- Deploy AI-driven threat detection to monitor suspicious data patterns and bot behavior.
- Secure critical infrastructure (energy grids, healthcare systems, financial networks) against cyberattacks.
- Invest in quantum-resistant encryption to prepare for next-generation threats.
2. Policy and Regulation
- Enforce transparency on social media platforms for political advertising and algorithmic decision-making.
- Develop national IW doctrines that define thresholds for retaliation and defense.
- Collaborate in international forums (e.g., UN, NATO) to establish digital conflict norms.
3. Societal Resilience
- Promote media literacy programs to help citizens identify disinformation.
- Engage civil society and NGOs in fact-checking and community outreach.
- Build trusted information ecosystems, including transparent communication from governments.

IV. Case Studies in Defense
- Estonia’s Cyber Defense League: A volunteer-based public-private partnership safeguarding the nation’s digital infrastructure.
- Taiwan’s Rapid Response Teams: Countering online disinformation in near-real time during elections.
- European Union’s Digital Services Act: Regulating tech companies to reduce the spread of harmful content.
V. Future Outlook
- AI Arms Race: Both attackers and defenders will increasingly rely on advanced machine learning tools.
- Metaverse and Virtual Platforms: New fronts for manipulation and identity-based targeting.
- Global Norms and Treaties: The need for international consensus to curb weaponized information.
VI. Policy Recommendations
- Prioritize cross-sector collaboration between governments, academia, and tech firms.
- Create rapid attribution mechanisms to identify perpetrators and hold them accountable.
- Encourage ethical innovation in AI and data governance to prevent misuse of emerging technologies.
- Increase investment in public education to foster critical thinking and trust in reliable information sources.
Conclusion
The battle against information warfare is not only technical but also psychological and cultural. While no system can be completely immune to manipulation, societies that cultivate transparency, resilience, and adaptive strategies will be far better positioned to withstand the onslaught of this invisible conflict.